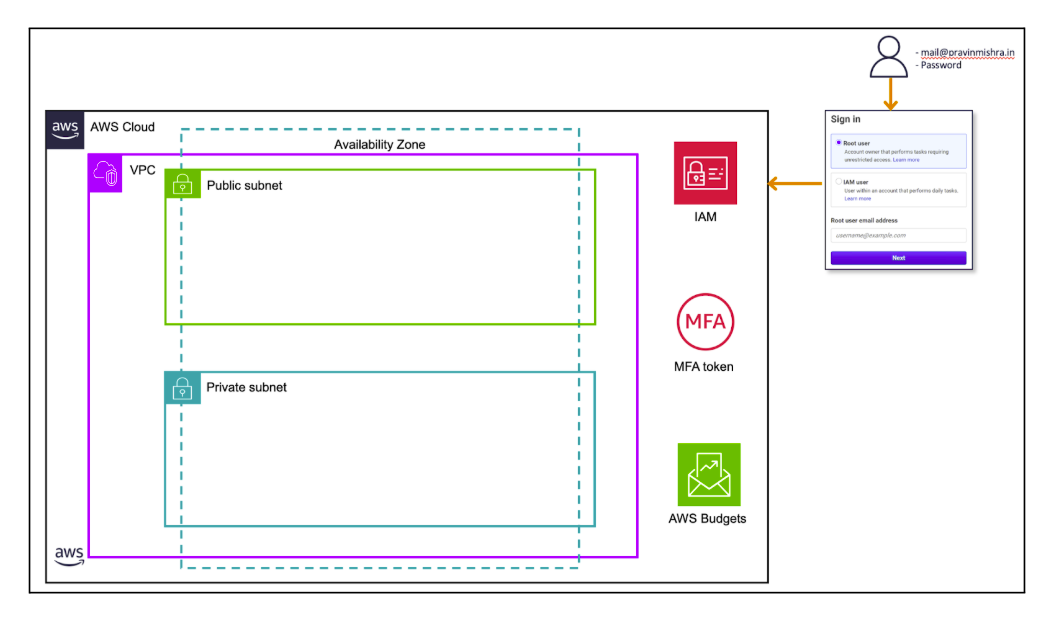
Growth of Technology The invention of computers really changed the whole world. It has played a big role in the development of science and technology. After the internet came, the world slowly turned into a global village.
Today people can’t imagine life without computers, mobile phones, or the internet. We depend on IT in almost everything — education, health, entertainment, communication. It’s no longer a choice, it’s a need.
Old College Syllabus But here is the issue. Technology is changing very fast, but our colleges are still teaching the same old syllabus.
...